In the wake of yesterday's news regarding CPU flaws and the vulnerabilities they open up, initially tied to Intel processors by a report by The Register, various IT goliaths have weighed in with their perspectives. The flaws detected have been dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715). Last night we updated the original story with a statement from Intel deflecting full blame for the situation from its products. Since then AMD, Google and Microsoft have all released statements. Here is a summary of what is being said at this time.

Google has published a much referenced blog post discussing these modern CPU vulnerabilities. The key findings are, as touched upon yesterday, that “malicious actors could take advantage of speculative execution to read system memory that should have been inaccessible”. Thus system memory containing passwords, encryption keys, or sensitive information open in applications could be accessed by an unauthorised party.
Importantly Google points the finger at “many CPUs, including those from AMD, ARM, and Intel,” and the various OSes that run on these platforms.
On the subject of its own products, Google says that Android devices with the latest security updates are already protected. Unfortunately the Android phone I bought in 2015 hasn’t had any Android updates in a year but core Google apps such as Gmail and Chrome still get updated which could help.
AMD
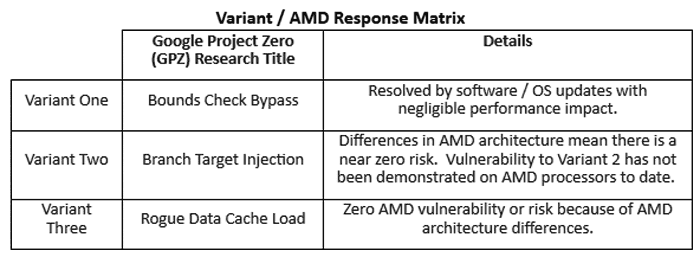
In an email to HEXUS, AMD stressed that its processors are subject to “near zero risk… at this time”. The statement says that it has actively engaged with the various security teams working on the recently disclosed risks and tabulates its products against the three speculative execution vulnerabilities detailed by Google.
Microsoft
Microsoft issued an unscheduled software update for all its currently supported OS versions last night. Security update KB4056890 offers mitigations for speculative execution side-channel attacks which would typically come via JavaScript code running in the browser.
As well as the patches noted above for Microsoft and Google OSes - Linux and MacOS are/will be patched shortly. To reassure its enterprise cloud customers Amazon has issued a statement about updates being put in place to protect AWS.
UPDATE for WIndows users:
If you are running a Microsoft WIndows OS please check through the following blog post by Microsoft. The January security patch might clash with your AV program and prevent your machine from starting. However, Microsoft is only offering the Windows security updates released on 3rd January 2018 to devices running anti-virus software from partners who have confirmed their software is compatible with the January 2018 Windows operating system security update.






