About a week ago HEXUS reported upon Intel's all-new patches for 6th-gen (Skylake, 100 series chipsets), 7th-gen (Kaby Lake, 200 series chipsets), and 8th-gen (Coffee Lake, 300 series chipsets) motherboards / CPUs. The firm had, at last, managed to update its updates and had tested them thoroughly enough to assure users that they wouldn't again be the cause of instability and random reboots.
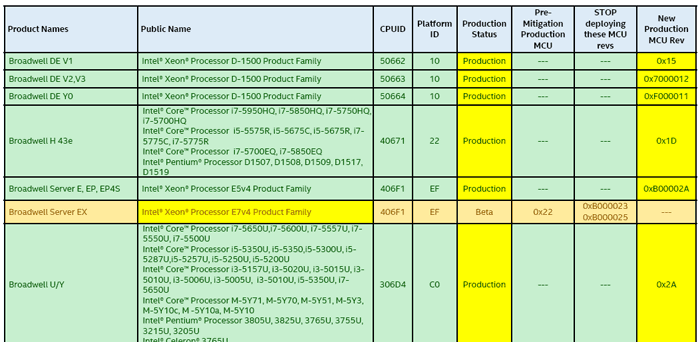
Intel has now refreshed its Microcode Update Guidance PDF to show that it has updated its fixes for Spectre vulnerabilities, for 4th-gen (Haswell) and 5th-gen (Broadwell) platforms. We know this because the Haswell and Broadwell parts in the guidance table are now highlighted in green which signifies "Intel has completed all validation and is authorizing customers to use this MCU in a production environment."
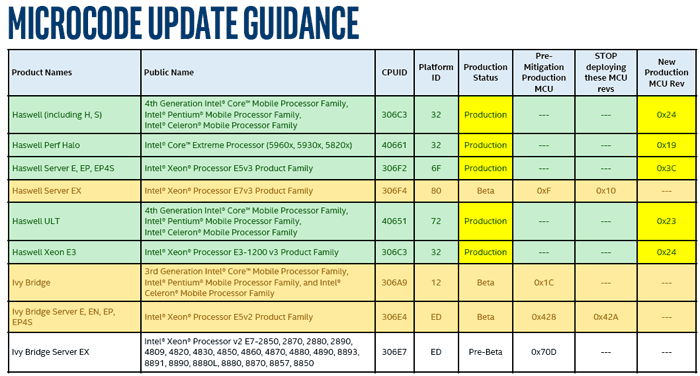
This is good news, as there are a lot of Haswell and Broadwell generation processor users out there. However this isn't the end of the story to get patched, it requires that your system vendor or motherboard vendor takes Intels update code and issues a BIOS update for you.
If you are a Sandy Bridge or Ivy Bridge platform user, consulting the new Microcode Guidance table, Intel's updated patches are still in beta at this time. Updates will go back even further than this though. It is indicated that there will be Spectre patches coming to processors / platforms as far back as Wolfdale (the Conroe die shrink from 2007).
Sadly, previous testing, including tests from Microsoft's labs, indicates that older processor models, and older versions of Windows, can run noticeably slower when patched.






