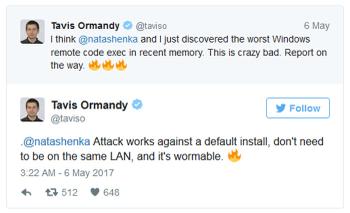
A couple of days ago Google Project Zero researchers alerted their Twitter followers, and Microsoft, of a 'crazy bad' Windows Defender bug. Tavis Ormandy said that he and Natalie Silvanovich had discovered "the worst Windows remote code exec in recent memory". In a follow up Tweet Ormandy told his followers that a remote code execution attack "works against a default (Windows) install," and that the attacker doesn't need to be on the same LAN to exploit this 'wormable' (potentially self-spreading) vulnerability.
To recap how big and how 'crazy bad' the Windows Defender bug was; it was possible for a hacker to craft a file that would have its malware payload executed by the built-in Windows anti-malware solution scanning it. Injected code could run with administrative privileges, so attackers could gain full control of the system, install spyware, steal or encrypt files, and so on. An attacker could IM or email you such a specially crafted file and even before you read the message the attachment could be wreaking havoc with your Windows PC system.
Microsoft's emergency security update arrived Monday night
Microsoft has responded rather quickly to being notified about the vulnerability by Google Project Zero. In Microsoft Security Advisory 4022344 it provides more details of the issues and of course a fix for the 'Microsoft Malware Protection Engine', at the heart of the problem.
Microsoft's advisory confirms the critical nature of the remote code execution flaw and how widespread it is - affecting Windows Defender in Windows 7, 8, 8.1, 10 default configurations as well as Microsoft's Endpoint and Forefront security software.
Your Windows PC should update within 48 hours of the security fix being issued (last night) but you can prompt an earlier install by manually checking via Windows Update. If the update has already completed you will have a Windows Defender engine version 1.1.13704.0 or higher.
Giving credit to Microsoft's swift action regarding this 'crazy bad' Windows Defender bug, Tavis Ormandy Tweeted a tribute to Redmond earlier this morning. "Still blown away at how quickly @msftsecurity responded to protect users, can't give enough kudos. Amazing." wrote the Project Zero researcher.