AMD recently shared some interesting technology preview slides at the 2019 Rice Oil & Gas HPC Conference. During the event, AMD SVP and GM of Data Centre and Embedded Soutions, Forrest Norrod, presented some slides entitled 'Evolving System Design for HPC: Next Generation CPU and Accelerator Technologies'. From what we can gather it looks like AMD plans to develop 3D chip stacking techniques, similar to what we have seen Intel propose with its Foveros 3D packaging.
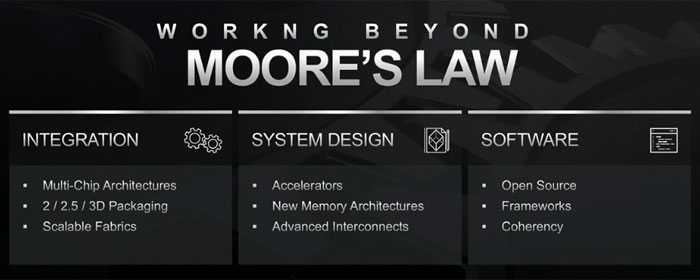
During his presentation Norrod explained that frequency scaling has ground to a halt over the last 10 years. "As we continually shrink our processes now, we don't get any more frequency, and really with this next node, without doing extraordinary things, we get less frequency," lamented the AMD SVP and GM.
In the near term AMD sees stacked memory architectures as the most beneficial tech-seam to mine. While AMD already stacks HMB2 memory next to GPU dies in its GPUs and APUs, Norrod explained that it wants to move to true 3D stacking in the near future. Doing so will provide even better bandwidth and performance for processors.
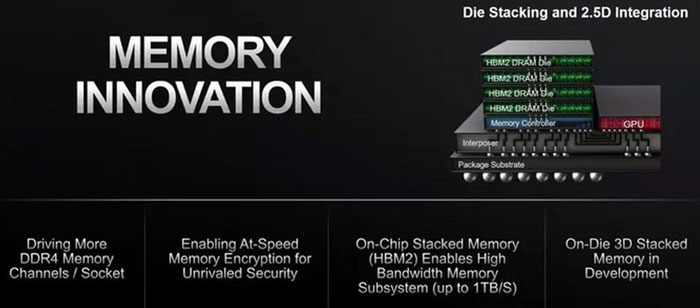
In a true 3D stacking design the memory would sit atop of the processor and be connected using vertical TSV (Through Silicon Via) connections. The proximilty and direct mating of the two dies increases performance and reduces power consumption, as well as affording density improvements.
Norrod's full presentation from the recent Rice Institute HPC event is embedded above.
Source: Tom's Hardware.
AMD – no SPOILERs
Earlier this month HEXUS reported upon another speculative execution based CPU vulnerability affecting Intel CPUs. AMD has now made a statement, saying that its processors don't need patching for the new SPIOLER vulnerability. Full statement is below:
"We are aware of the report of a new security exploit called SPOILER which can gain access to partial address information during load operations. We believe that our products are not susceptible to this issue because of our unique processor architecture. The SPOILER exploit can gain access to partial address information above address bit 11 during load operations. We believe that our products are not susceptible to this issue because AMD processors do not use partial address matches above address bit 11 when resolving load conflicts."






