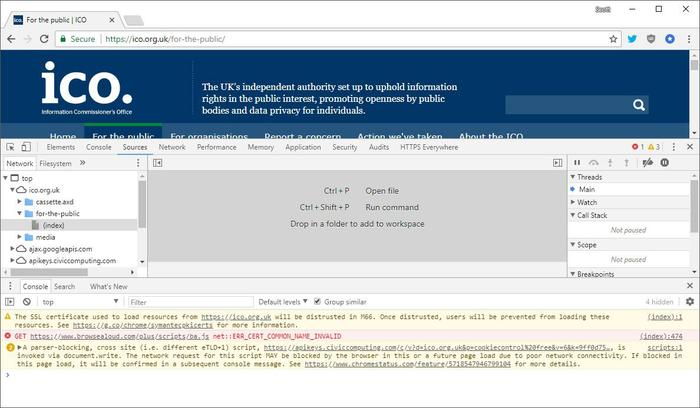
It has been discovered that thousands of governmental websites, mainly in the UK, Ireland, Australia, Sweden and the US, are running Coinhive's Monero mining script on visiting computers. What all the affected sites have in common is that they use an accessibility plugin called Browsealoud - which ordinarily facilitates easy speech, reading and translation tools. Hackers have managed to compromise the Browsealoud plugin in some way and get it to run the crypto-mining code.

Example government websites running the Coinhive script in the UK include:
- Student Loan Company
- Information Commissioner’s Office
- Financial Ombudsman Service
- Various .nhs.uk hospitals
- Many council websites
click to zoom
Affected websites in other countries cover similar ground - sites which would benefit from the accessibility benefits provided by the Browsealoud plugin. US-based examples are the US courts system's websites and Indiana Government sites.
HEXUS has previously covered the use of the Javascript-based Monero coin mining, as used by the Pirate Bay as an alternative to ad-funding. Late last year the first tales of cryptojacking came to light where sites secretly run mining scripts to make cash from visitor CPU time. In January such scripts were even found inside adverts injected by Google's DoubleClick ad on YouTube.
With the thousands of governmental websites found to be affected by the crypto-jacker this weekend, we expect today to be busy for webmasters and system administrators. They will have to digest all the information about the cryptojacking problem and decide what to do.
click to zoom
Texthelp, authors of the Browsealoud plugin, have taken the service offline and claims to have already addressed the malware issue in an update. However, the plugin will remain offline until 12 noon (GMT) on Tuesday to give customers time to learn about the underlying issue and response plan. Texthelp is also investigating the "criminal act," of the cyber attack on its servers, which resulted in a compromised JavaScript file being injected into the Browsealoud product.
The UK's NCSC (National Cyber Security Centre) made the following statement yesterday:
"NCSC technical experts are examining data involving incidents of malware being used to illegally mine cryptocurrency.
The affected service has been taken offline, largely mitigating the issue. Government websites continue to operate securely.
At this stage there is nothing to suggest that members of the public are at risk."