Another vulnerability has been discovered in Intel CPUs. Again, Intel CPUs have been found to be prey to a speculative execution attack, but previous generation software and hardware patches haven't closed off this particular vulnerability. The Researchers who discovered 'L1D Eviction Sampling' vulnerability have dubbed it CacheOut as the side-channel weakness exploited is in the CPU caching mechanism.

Before we go on, it is worth noting that Intel CPUs released before SkyLake and after Q4 2018 will not be vulnerable to CacheOut. AMD processors aren't affected, according to the researchers. IBM and ARM processors might be affected but were outside the scope of the paper.
Intel has previously made efforts to limit the chance of side cannel attacks and hackers 'drinking from the data firehose' by overwriting data buffers in the CPU. However, CacheOut is a new Microarchitectural Data Sampling (MDS) technique that can bypass these countermeasures.

Researchers at the University of Michigan and University of Adelaide observed that "as data is being evicted from the CPU L1 cache, it is often transferred back to the leaky CPU buffers where it can be recovered by the attacker." An attractive aspect of CacheOut for hackers is that it allows choice of which data to leak from the CPU’s L1 cache, as well as which part of a cache line to leak. The researchers demonstrated that it is possible to "leak information across multiple security boundaries, including those between hyperthreads, processes, and virtual machines, and between user space and the operating system kernel, and from SGX enclaves." Intel has classed CacheOut, or L1D Eviction Sampling / CVE-2020-0549 / INTEL-SA-00329 - as a medium severity level 6.5 vulnerability.
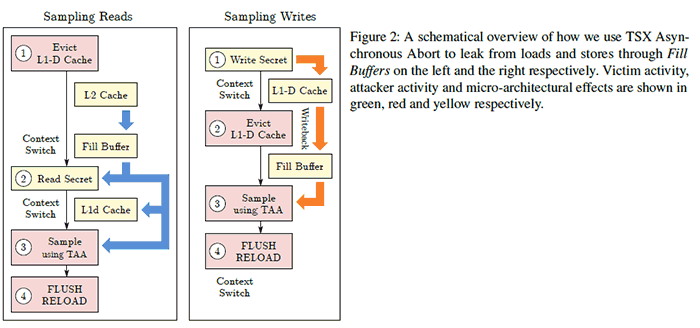
The security researchers got in touch with Intel last year before making their research public. This helped Intel get patches ready, and cloud providers have already deployed countermeasures against the flaw. Disabling hyperthreading or disabling TSX within Intel’s processors can mitigate against the flaw for now. However, Intel says it expects to release microcode updates for affected processors shortly.






