A group of academics and researchers from several universities and Bitdefender have shared details of a new class of transient-execution attacks exploiting microarchitectural flaws in Intel CPUs. In essence, the CPU flaw has been characterised as allowing 'reverse Meltdown' attacks where instead of a hacker extracting data from the processors buffers or caches, they would instead inject malicious code into the processing pipeline for nefarious purposes. In this way it is said to be possible to "steal sensitive data and keys from Intel SGX," the secure enclaves in modern Intel processors.
The new attack is called Load Value Injection or LVI, and a dedicated website has been set up with descriptive texts, videos, and a handy FAQ. As touched upon in the intro paragraph, LVI turns previous data extraction attacks around and, importantly, defeats all existing mitigations at the software and hardware levels. The researchers assert that "LVI is much harder to mitigate than previous attacks, as it can affect virtually any access to memory."
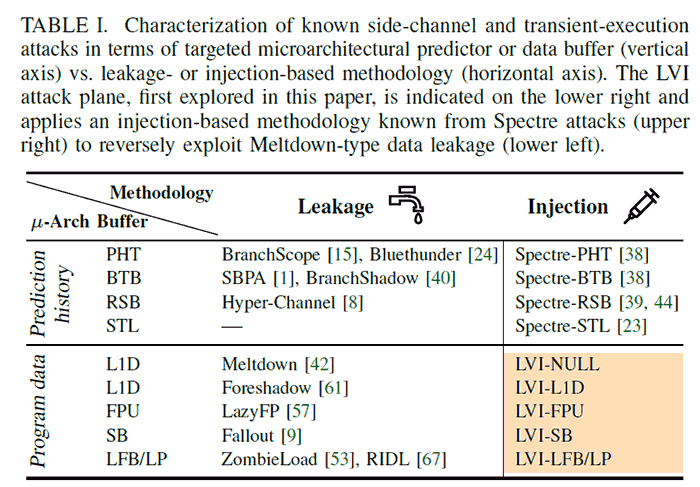
Handily the researchers summarise the exploitation of LVI in four simple-ish steps, as follows:
- Poison a hidden processor buffer with attacker values.
- Induce a faulting or assisted load in the victim program.
- The attacker's value is transiently injected into code gadgets following the faulting load in the victim program.
- Side channels may leave secret-dependent traces, before the processor detects the mistake and rolls back all operations.
Sadly, LVI bypasses all existing mitigations for the likes of Meltdown, Spectre, Foreshadow, ZombieLoad, RIDL, and Fallout. The researchers say that it won't be possible to transparently patch this vulnerability with a microcode update. Rather, at this time, a computationally expensive software update will need to be applied "to serialize the processor pipeline and disable speculation after potentially every load operation," and in the future silicon fixes will be applied to mitigate LVI in hardware.
Intel is releasing an update for the Intel SGX SDK to assist SGX application providers in updating their enclave code. For other guidance, please review Intel’s white paper here. SGX became a feature of Intel Core processors from Skylake onwards, however Ice Lake chips that have been tested seem to be unaffected by LVI. Due to the Intel SGX attack vector, LVI as described by the researchers specifically applies to Intel processors.
Performance impact
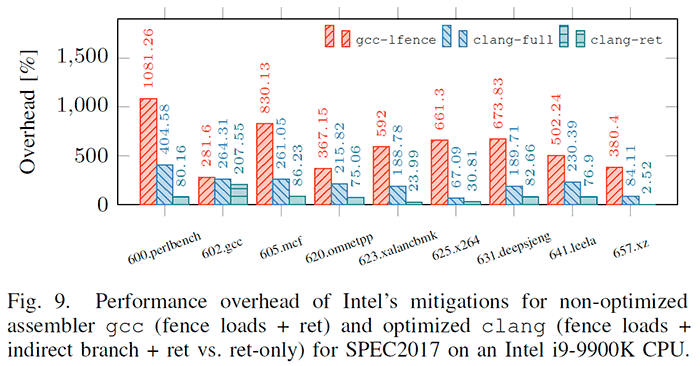
According to testing done by the researchers, the performance overhead of Intel's mitigations are quite impactful. Depending on the calculations type things can slow down from 2 to 19 times.
Intel's opinion
Intel has set up a page in its developer zone discussing Load Value Injection / CVE-2020-0551 / INTEL-SA-00334. It classes the flaw as being of medium severity. However, it essentially claims that "LVI is not a practical exploit in real-world environments where the OS and VMM are trusted," due to the numerous complex requirements that must be satisfied to affect the hack.
With the performance overheads of the software mitigations in mind, and the threat model, Intel encourages sys-admins and developers to carefully consider whether to patch to mitigate against LVI at this time.
Last but not least, it is interesting to see Daniel Gruss (of the Graz University of Technology) credited again, as one of the team here. Gruss was under the spotlight when the report into AMD's L1D exploits became public as he receives some funding from Intel. For work on LVI, it appears that Gruss and his colleagues received funding from many sources including academic funds and grants - as well as from processor designers like Intel, Arm, and AMD.






