The Meltdown and Spectre security issues saga has been running for over a week now. At first it seemed to be an Intel-only problem but later we found that nearly every modern processor was potentially vulnerable from one or more of the trio of attack methods. Then there was the question of the performance impacts from the security patches that were hurriedly being prepared. Just ahead of the weekend Intel asserted that the necessary CPU patch performance impacts would be minimal in the real world “for the average computer user… and will be mitigated over time”. At the same time Intel supplied substantiative quotes from the likes of Apple, Microsoft, Amazon and Google. Now Microsoft seems to have adjusted its outlook, particularly for general PC use.
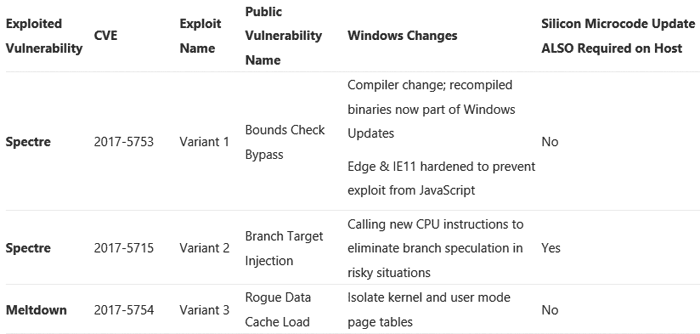
Terry Myerson, Executive Vice President, Windows and Devices Group, wrote a piece on this very topic yesterday. The blog post discussed the trio of vulnerabilities under the Meltdown and Spectre classifications (outlined above). Myerson went on to talk-up Microsoft’s efforts in mitigating the vulnerabilities; he said out of the currently supported 45 versions of Windows, 41 had already been updated, with the rest due to be patched soon.
Importantly Myerson said that previous benchmarks had not been completed with both the necessary OS and silicon updates and he addressed this directly with a bullet point summary of performance findings as below:
- With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds.
- With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance.
- With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance.
- Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment.
From the above it seems that if you have an older pre-Skylake system running the likes of Windows 7 or 8 you will surely notice some system speed impacts. Furthermore, if the said machine is used for any server duties and/or IO-intensive application it will feel even worse.
Myerson explained that Microsoft’s newest OS, Windows 10 has less user-kernel transitions so performs better when patched, and CPUs such as Skylake and beyond have refined instructions to disable branch speculation. The data sets behind the above bullet points will be shared in the coming weeks, said Microsoft’s Myerson.
MSI releases multitude of BIOS updates to address recent security vulnerabilities.
In news related to the above, MSI has pushed out BIOS updates for its range of Z370-series motherboards. Meanwhile it continues to work on updates for its its X299-series, 200-series, 100-series and X99-series motherboards. You can read more and find the download links here.







