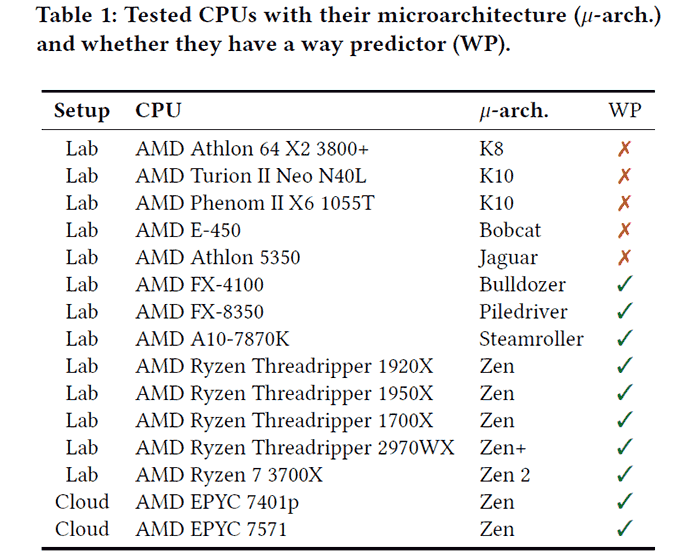
This weekend there has been a lot of chitter-chatter on social media about a new research paper published by academics from the Graz University of Technology in Austria. 'Take Away: Exploring the Security Implications of AMD's CacheWay Predictors' talks about two new claimed AMD CPU side channel vulnerabilities dubbed Collide + Probe and Load + Reload.
The researchers say the AMD L1 cache way predictor architecture present in all its CPUs since 2011 allows these attack techniques to work. You can check out the research in full by downloading this PDF. However, there is some controversy about one of the research professors being Intel 'sponsored' (see this Twitter link and its replies). Additionally, AMD all but dismissed the concerns brought to light by the Graz researchers in an official security bulletin published on Saturday.
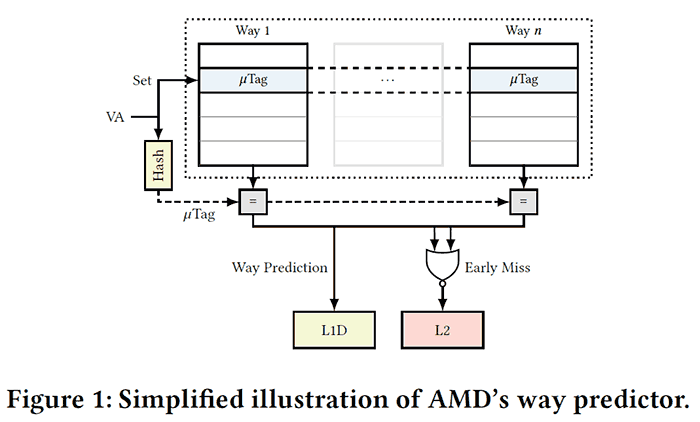
You can read more about the claimed potential security exploits in AMD CPUs from the white paper linked in the intro. In brief the 'Take A Way' flaws can be summarised as follows. Firstly the researchers reverse engineered AMD's modern L1D cache way predictor which was designed to reduce processor power consumption by improving the way the CPU handles cached data. Herein the purported weakness lies. All AMD processors since Bulldozer have this speed-up feature built-in. Knowledge of an "undocumented hashing function" of the L1D cache formed the basis of the new attack techniques.
- Collide+Probe: "an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core."
- Load+ Reload: "we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core. While Load+Reload relies on shared memory, it does not invalidate the cache line, allowing stealthier attacks that do not induce any last level-cache evictions."
The researchers go on to document the way their attacks work and provide some case studies and examples of attacks. They assert that the research shows that AMD's CPU design with L1D cache is demonstrably "vulnerable to sidechannel attacks". The attacks could be used in the real world, say the researchers, without needing physical access to the computers, and without specialised equipment.
Notably, vectors where the attacks could be used include via Javascript or in a cloud computing environment - even in fully up to date and patched systems. Examples given are as follows:
- We established a high-speed covert channel and utilized it in a Spectre attack to leak secret data from the kernel.
- We reduced the entropy of different ASLR ( (address space layout randomisation) implementations from native code and sandboxed JavaScript.
- We recovered a key from a vulnerable AES implementation.
AMD was apparently notified of these findings last August so the company has had some time to react and look at updates to counter 'Take A Way' flaws / exploits. However, AMD's official response has been short and rather dismissive. There currently seems to be a disagreement about whether systems with fully updated OS, firmware and software are vulnerable to Collide + Probe and Load + Reload exploits...
Looking at the bigger picture, the Take A Way vulnerabilities aren't / weren't that severe. In Daniel Gruss's own words - the professor who is controversially 'sponsored' by Intel - "The attacks leak a few bits of meta-data. Meltdown and Zombieload leak tons of actual data." (For quote see Twitter relies to the link in para 2)






