Yesterday there was a lot of media coverage concerning the KRACK WPA2 vulnerability. News broke that attackers could decrypt packets on WPA and WPA2 networks by manipulating and replaying cryptographic handshake messages between client devices and access points. This could enable these third parties to read unencrypted data transfers or even inject malware into websites being browsed.
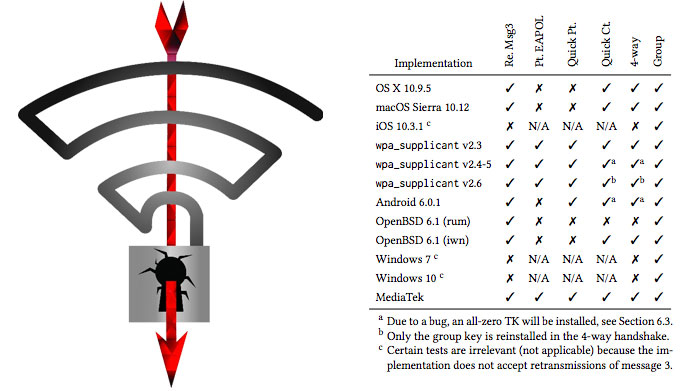
KRACK is an acronym for Key Reinstallation Attacks and is particularly bad news for Android 6 and Linux (wpa_supplicant), which can be tricked into (re)installing an all-zero encryption key. There are several implementations of the KRACK attack possible and OSes vary in their resistance, as illustrated in the table above. However, there is no data suggesting this vulnerability is being exploited in the wild at the time of writing.
Microsoft patched for KRACK last Tuesday
Microsoft’s Windows 7 or newer OSes have already been updated to patch for KRACK vulnerabilities. If you have automatic updates turned on, then from last Tuesday onwards you will have received security updates directly addressing KRACK. You can read about the supplied Windows fix in an advisory document: CVE-2017-13080.
On Patch Tuesday last week this fix was provided but Microsoft didn’t disclose it in the release notes, as the vulnerability was yet to go public.
Android updates
According to The Verge, Google has promised an update for affected devices “in the coming weeks”. As Android 6+ has been highlighted as one of the most vulnerable OSes with regard to this attack, updates could be seen as important. Google Pixel devices should be updated by 6th Nov but other phone brands will undoubtedly lag behind in the race to update.
Apple’s iOS and MacOS devices have already got KRACK patches in beta versions, so fixes for these should appear in coming weeks.






