Researchers from the Worcester Polytechnic Institute, Massachusetts, USA and the University of Lübeck, Germany have published a paper (PDF link) detailing a new speculative execution security flaw present in all modern Intel Core processors. The flaw has been dubbed 'SPOILER' which is some kind of shorthand for 'Speculative Load Hazards Boost Rowhammer and Cache Attacks'. In brief it is possible to use SPOILER vioa malicious JavaScript in a web browser or some malware to extract passwords, keys, and other data from memory.
The 'speculative execution' CPU performance enhancing technique that is prey to SPOILER might remind one of the well known Spectre vulnerabilities first publicised in January 2018. However SPOILER's data leakage "stems from a completely different hardware unit, the Memory Order Buffer," write the researchers. Thus it isn't currently mitigated by current Spectre patches.
"Spoiler is not a Spectre attack. The root cause for Spoiler is a weakness in the address speculation of Intel's proprietary implementation of the memory subsystem which directly leaks timing behaviour due to physical address conflicts." Via this novel microarchitectural leakage critical information is revealed "about physical page mappings to user space processes". Discussing the technique in more depth the researchers added "To exploit the leakage, we used the speculative load behaviour after jamming the store buffer."
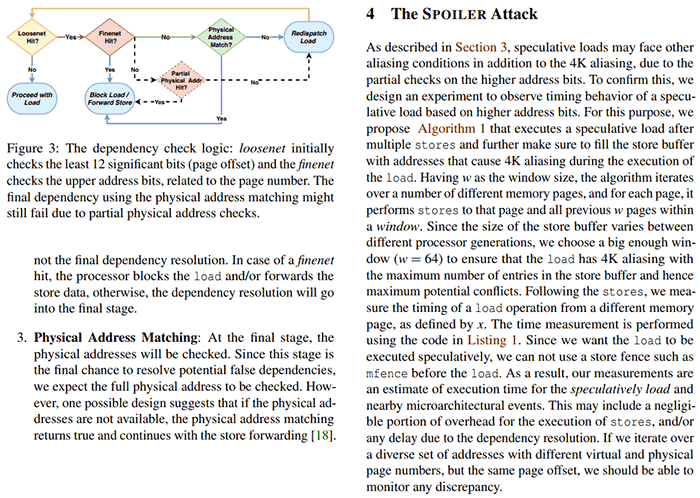
Importantly the SPOILER vulnerability can cause leakages in user space with no special privileges, on any OS, and works from within virtual machines and sandboxed environments. Leaked data from SPOILER attacks isn't useful on its own but can help speed up existing attacks more efficiently, or to devise new attacks using the novel knowledge.
The research team got in touch with Intel about SPOILER on 1st Dec 2018.
Since this news hit the wires sometime yesterday, an Intel spokesperson has been quoted by The Register, providing official reaction. The spokesman said "we expect that software can be protected against such issues by employing side channel safe development practices. This includes avoiding control flows that are dependent on the data of interest. We likewise expect that DRAM modules mitigated against Rowhammer style attacks remain protected."






