Microsoft's Virtualization-Based Security (VBS) was introduced with Windows 10. This is a security enhancing setting that by default is turned off, but some enterprise admins might apply it to the machines they manage. With the advent of Windows 11, Microsoft is making a change to VBS defaults – and with its partners it is going to be enabling VBS (and Hypervisor-protected Code Integrity - HVCI) by default "on most new PCs".
"VBS uses hardware virtualization features to create and isolate a secure region of memory from the normal operating system. Windows can use this 'virtual secure mode' to host a number of security solutions, providing them with greatly increased protection from vulnerabilities in the operating system, and preventing the use of malicious exploits which attempt to defeat protections."
People keeping up with Windows 11 news will be well aware that Microsoft is trying to set it up as a rock steady and secure OS from the outset, and this is part of the reasons for the stringent modern hardware requirements (only the newest processor generations and TPM requirement). It turns out that slightly below spec processors like the AMD Ryzen 1000 series, or 6th/7th gen Intel CPUs, don't have Mode Based Execution Control (MBEC) hardware so will feel quite a performance hit with VBS turned on.

If you upgrade your Windows 10 machine to Windows 11, it won't toggle VBS and HVCI on – it will inherit your settings. However, if you do a clean installation of Windows 11 these (potentially performance sapping) security features will be on by default. UL Benchmarks has noticed this, so is going to be adding VBS detection to its benchmarks to help users compare like with like, going forward.
You are probably interested in the performance impacts that might be observed on machines with VBS (and HVCI) on and off. Thankfully both ComputerBase (German) and PC Gamer have done some benchmarking to help inform users of the potential impacts. In summary, at its worst, the security settings can slow your PC gaming/app experience by as much as 28 per cent – ouch.
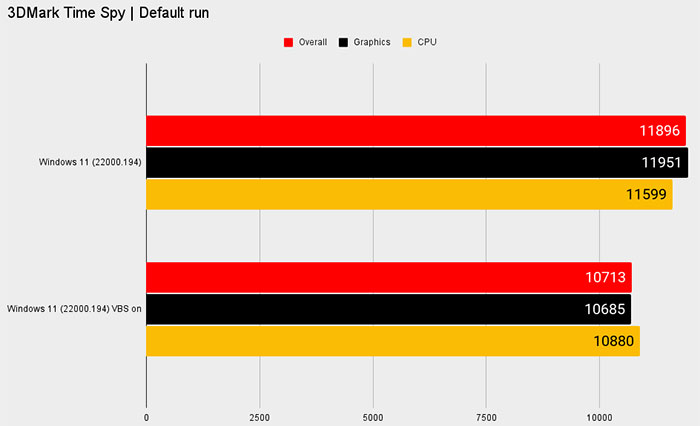
You can check both the ComputerBase and PC Gamer results, as they both test many games, and as you expect the impact of toggling this security is variable. PC Gamer nicely sums up the findings, verbally, as follows; "Far Cry New Dawn is the outlier here, which barely shrugs at VBS, with just a 5% reduction in frame rate. But Horizon Zero Dawn drops by some 25%, Metro Exodus by 24%, and Shadow of the Tomb Raider by 28%. Interestingly, the 3DMark Time Spy score only dropped by 10%."
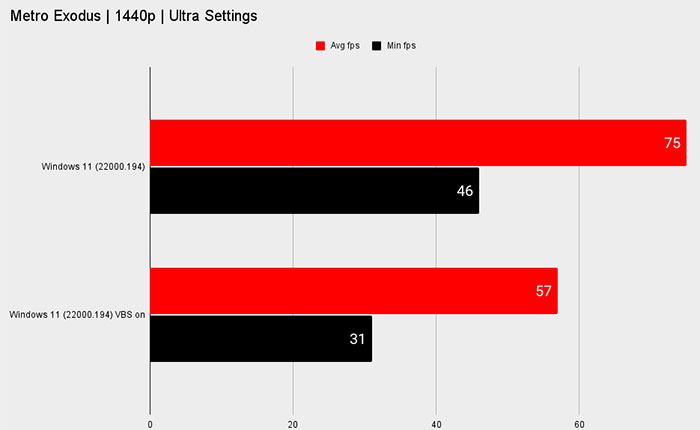
In summary, this is something that I think enthusiasts will have to watch out for, especially when building new PCs with Windows 11 clean installations. Some of the gaming performance impacts seem so severe that it will be interesting to see if Microsoft partners like Dell, HP, and Lenovo will stomach them on their pre-built gaming PCs.
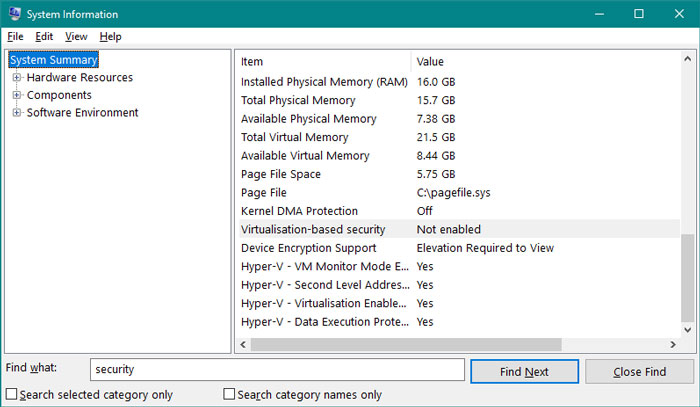
My Windows 10 laptop has VBS disabled, I've never changed this setting.
Microsoft has heralded Windows 11 as being "made for" gaming, so there needs to be some work done here with updates, patches or policies before gaming PCs with VBS and HVCI toggled on hit shelves.






