There has been a nasty NTFS corruption bug present in Windows 10 for nearly three years. It is also present in some older Windows XP versions. Just ahead of the weekend The Verge highlighted that a user browsing "a specially crafted line inside a ZIP file, folder, or even a simple Windows shortcut," in Explorer is enough to trigger the bug which will corrupt your file system. Bleeping computer also looked at the bug and tested how it works.
Security researcher Jonas L has warned about this NTFS vulnerability several times, starting H2 2020, before it was picked up by media and Microsoft announced that it is "aware of this issue and will provide and update in a future release," for Windows 10. Microsoft added that anyone wishing to do any malicious works via the bug would have to rely on persuading the victim to download or accept a file transfer - social engineering.
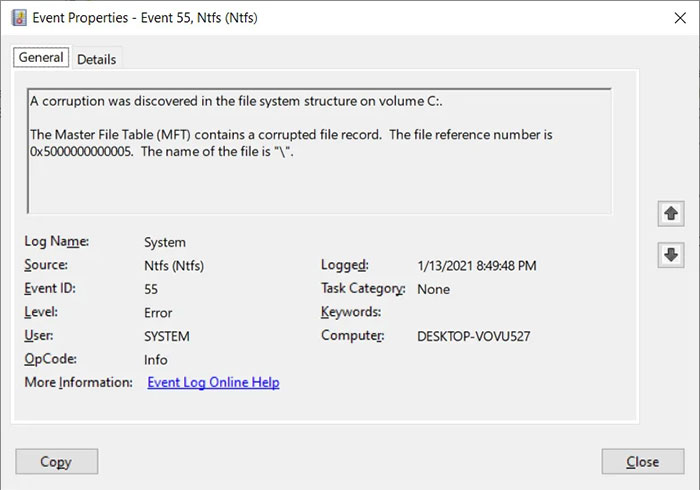
So, what is the problem? Starting from approx Windows 10 build 1803 and continuing until now, an NTFS drive can be corrupted by merely trying to access the $i30 attribute. An example command that would corrupt a Windows 10 system, provided by Bleeping Computer to illustrate the scarily simple issues is shown below:
cd c:\:$i30:$bitmap
The potential for mischief is pretty sizable. The corruption issue can be triggered very easily if a user creates a Windows shortcut file (.url) with its icon location set to the path in the command. Then if any recipient views a folder with this file in (on Windows 10) then drive corruption may result. Malicious actors could distribute this file via Zip archives, HTML files or other ways.
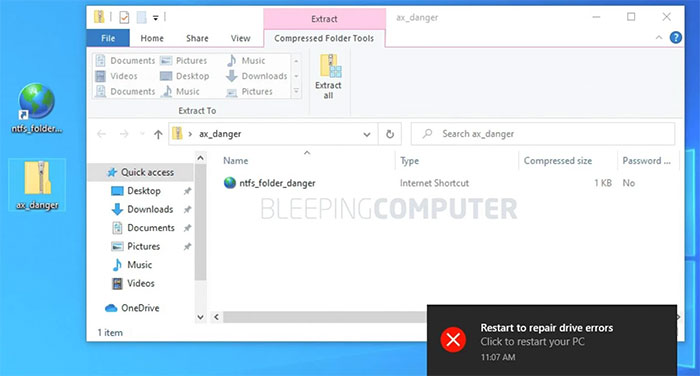
Simply opening this downloaded ZIP file was enough
In Bleeping Computers tests it was noted that sometimes that chkdsk could sometimes repair the file system on reboot and clear the contents of the icon file with path set to c:\:$i30:$bitmap.
Another, less serious, issue has been shared by Jonas L in recent days. Again it involves Windows tripping over a path but this time causing a BSOD. OK, your machine will typically restart after a BSOD and return to normal but Jonas L noted that threat actors could possibly work out how to abuse the bug for remote code execution, elevation of privileges, or some kind of denial of service chicanery.
All screenshots from Bleeping Computer.






